| Subtotal | $0.00 |
| Subtotal | $0.00 |
Users with Windows servers may sometimes receive an "untrusted connection" error, when connecting to their websites, despite the fact that a PKCS#7 certificate with the full chain was imported on the server. The issue is more frequent on mobile devices, rather than on desktop machines, and occurs most commonly with Sectigo certificates.
When checking the certificate installation in an online checker, you will see that the certificate is returned with one intermediate.
To understand what causes the issue and how to overcome it, we will provide a better understanding on how Windows servers work with SSL certificates. First, remember that Windows servers do not return root certificates during SSL handshake and they build up certificate chains using the shortest way they can find.
Let us investigate this issue using the example of a Sectigo PositiveSSL certificate. PositiveSSL (and other Sectigo certificates) has two variants of CA chain. One ends up with SHA-1 root certificate and the other is completed by a newer SHA-2 root, which is not included in trusted stores of most mobile devices and might be missing in old versions of desktop browsers.
After certificate installation in Windows, your server may contain self-signed Sectigo Public Server Authentication Root R46 root certificate. Some older devices may not trust this self-signed certificate, and the workaround to this issue is to install cross-signed Sectigo Public Server Authentication Root R36 certificate and trusted USERTrust RSA Certification Authority root. This should complete the certificate chain properly on both new and old devices. However, Windows servers prefer using shorter certificate chains, making cross-signed certificate unusable. In order to mitigate this, the self-signed root Sectigo Public Server Authentication Root R46 certificate has to be disabled.
In order to overcome the issue, you’ll need to disable the usage of the root certificate that prevents building a proper certificate chain. Follow the steps below:

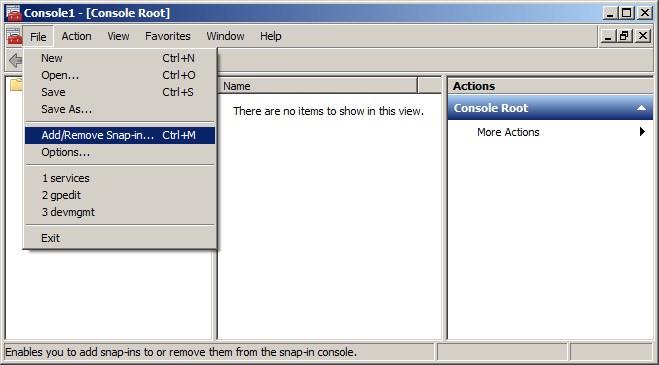



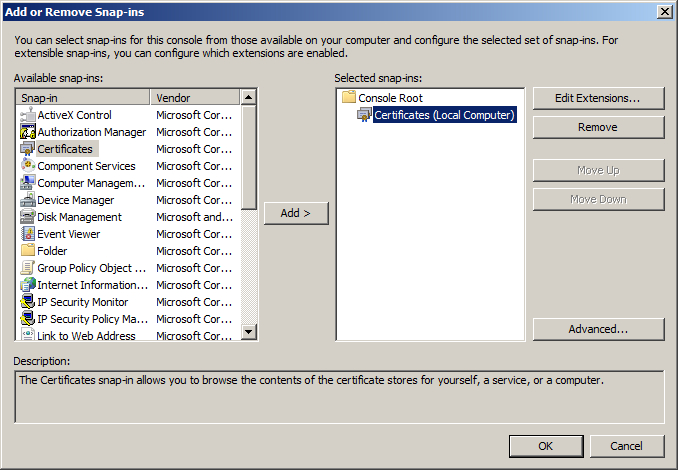

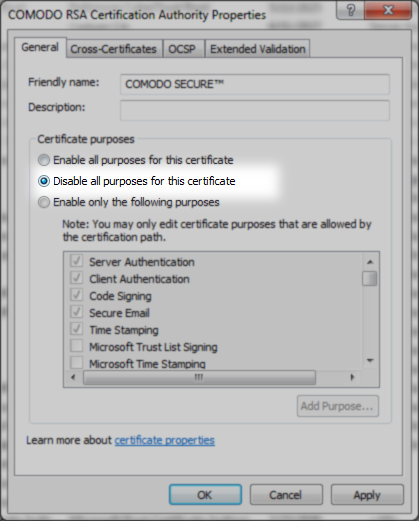
This should resolve the issue with the certificate chain returned by the Windows server and remove all the warnings in browser.
Need help? We're always here for you.